Getting Started with Embedded Systems: A Comprehensive Guide
An introduction to embedded systems development, covering hardware basics, programming fundamentals, and practical project examples.
Insights, tutorials, and thoughts on technology, embedded systems, and software development

An introduction to embedded systems development, covering hardware basics, programming fundamentals, and practical project examples.
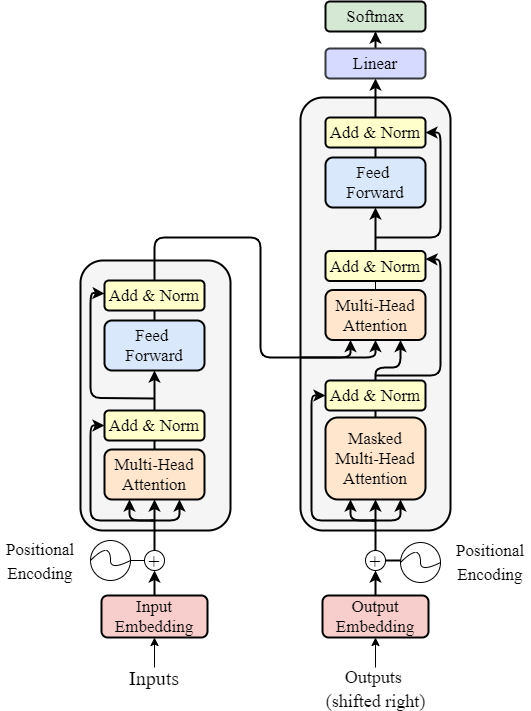
Exploring practical applications of deep learning, including real-world case studies and implementation strategies.
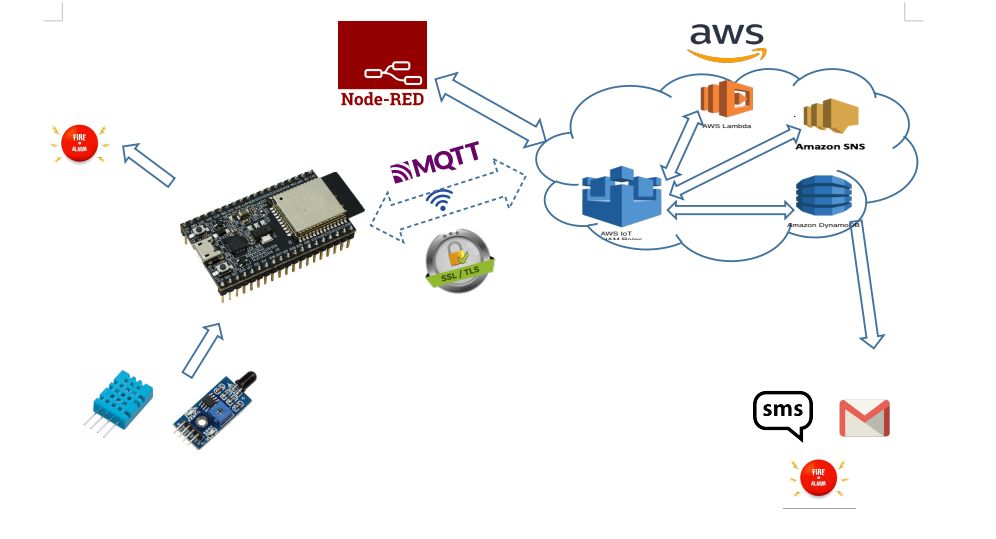
Design patterns and best practices for creating robust and scalable Internet of Things applications.